Why practical security will make your apps more secure
Hey there!
There's more to security than just policy documents. You can't just work your way through a checklist to keep everything secure, and your users happy. You need to know what to focus on and what are the most important risks affecting your applications. This is why I teach security from a practical point of view, why I demo live hacking at conferences, and why my new course is called Practical Laravel Security.
Something happened this week that really highlighted to me why learning security in a practical way is so important. Let me tell you about it...
In my last update, I talked about making the course app that will power Practical Laravel Security as secure as possible, and that I was planning on using a new authentication package to provide of some nice Multi-Factor Authentication (MFA) options. Since I sent out that email, Claudio Dekker released his Laravel Auth package, and I've spent the past week building the course app and integrating the package.
It's still a very early version, so there is a lot of styling and front-end work to be done, but something in how he built the package really jumped out at me: picking the right secuirty level for your app. Or to phrase it another way: practical security.
I was chatting to Claudio about his package and one of his technical requirements is for a high-secuirty implementation. One of his identified risks is email-based password resets being vulnerable to account take-over in the scenario where the email account itself is compromised. And let's be honest, this is a massive risk. Most of the websites we log into are vulnerable if someone can hijack our email accounts!
His solution was to implement a recovery key, generated by the app and shared with you once. In order to reset your account without the password, you need to click a verification link sent via email and provide the recovery key that you stored from when you created your account.
Now, if you're like me, you'll have stored that next to your password in your password manager! On the surface it doesn't sound overly helpful, but when you consider having Multi-Factor Authnetication (MFA) on your account too, that can be lost (i.e. Losing your phone, or your hardware key) independant of your password and suddenly the recovery key makes sense.
However, this level of security relies on users who need their accounts to be secure even if their email accounts are compromised. I personally have very few accounts that are more sensitive than my email account during a breach. For the ones which aren't as sensitive, being able to reset my password via email is totally fine. It's a risk I accept, and I keep my email accounts locked down.
This is what I mean by Practical Security!
When thinking about the security aspects of your apps, you need to consider the practical aspects of your decisions. Think about who your users are and what data you are storing. Think about who is likely to be attacking your app and what they could be after. Both of these will help you determine the right risk level and security controls, but at the same time not making it overly hard for your users to use your app.
This is exactly the sort of thing I teach you in Practical Laravel Security. A big focus of the course is teaching you not only how the different security features in Laravel work, but when to use them and why. By the end of the course, you'll know exactly when to use multi-factor authentication, authentication methods, password attacks, and more.
Presale & Early Access...
Practical Laravel Security is currently open for presales, at the discounted price of $249 USD (full price $500 USD).
Due to the interactive nature of the course, I will be opening up the first modules and launching Early Access this coming Friday (16th Dec). Subsequent modules will be released as they are ready over the coming months.
The current presale price will be ending on Friday, so now is definitely the time to get the presale discount!
(If you're interested in teams, student, or PPP pricing, please reach out to me directly.)
I'm considering a dedicated Slack or Discord as a bonus, as a way to discuss the modules and challenges. If anyone has experience setting one of these up for a course like this, please reach out! Discord scares me and my experience with Slack is limited...
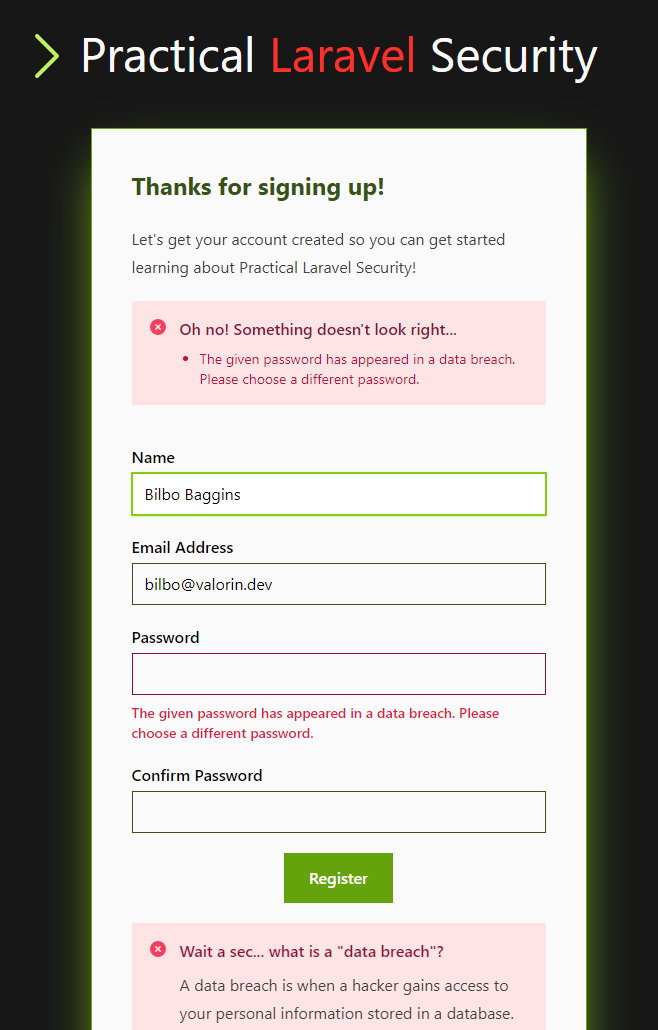
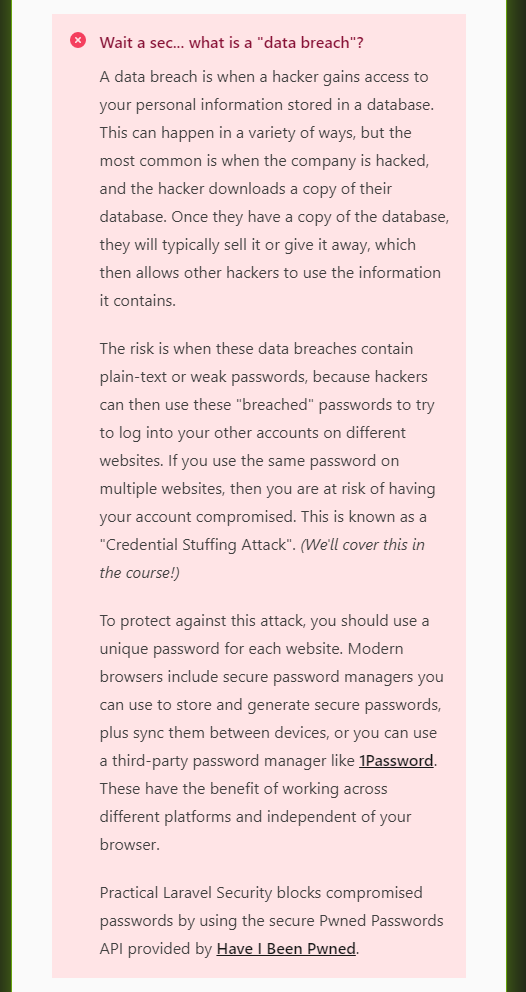
Blocking Compromised Passwords
Before we finish up, I wanted to share some screenshots showing how blocking compromised/pwned passwords is going to work in the course app.
|
|
We will be covering all of this within the course, both the theory behind why and how the attacks work, and the practical aspects of actually adding this sort of notice.
Ok my friends, that is all I wanted to cover today. I hope you enjoy the rest of your weekend and I'll reach out again soon! Hopefully with news of the Early-Access. 😁
Thanks,
Stephen
P.s. Yikes, my coding skills are rusty! I've spent the past year auditing sites, reading code, and writing reports and articles... but not much coding, and some of this front end scaffolding stuff is driving me nuts!