CSRF protection with CORS & SameSite Cookies
Hey there,
I'm excited to let know know that just released two new modules for Practical Laravel Security: SameSite Cookies, and Cross-Origin Resource Sharing (CORS)! 😁
These two modules join with CSRF Tokens to finish out our Cross-Site Request Forgery (CSRF) module, and teach you everything you need to know to defend your Laravel apps from CSRF attacks. Although it's super easy to exploit and difficult to defend against, CSRF is often treated as a solved problem. However, all it takes is a single misconfiguration in your defences to leave an endpoint exposed and vulnerable to attack.
For those who are unfamiliar with CORS and/or SameSite Cookies:
CORS is a way for your application to define what resources in your app are available to different domains. It allows you to provide an easily consumable API while still protecting sensitive information and preventing your CSRF tokens from being stolen and exploited. It is an essential piece in protecting against CSRF attacks.
SameSite Cookies are cookie attributes that instruct the browser which cross-site requests the cookies are allowed to be included on. It allows you to protect sensitive endpoints from being called and exploited by external sites, while supporting user friendly navigation.
If you've already signed up for Practical Laravel Security, head over to the Defend section to check them out:
What's Next?
Now that we've wrapped up CSRF attacks, we're moving on to SQL Injection (SQLi)!
This is going to be a fun module to tackle, and I've got some great challenges planned. SQLi is another "solved problem" that keeps popping up around the place. It's easy to avoid, but also easy to overlook when building your queries.
I've built SQLi challenges before, for my Laravel Security in Depth mailing list, so I'll be taking some inspiration from there and should be able to get them working pretty quickly. So keep an eye out! 😁
Challenge Update
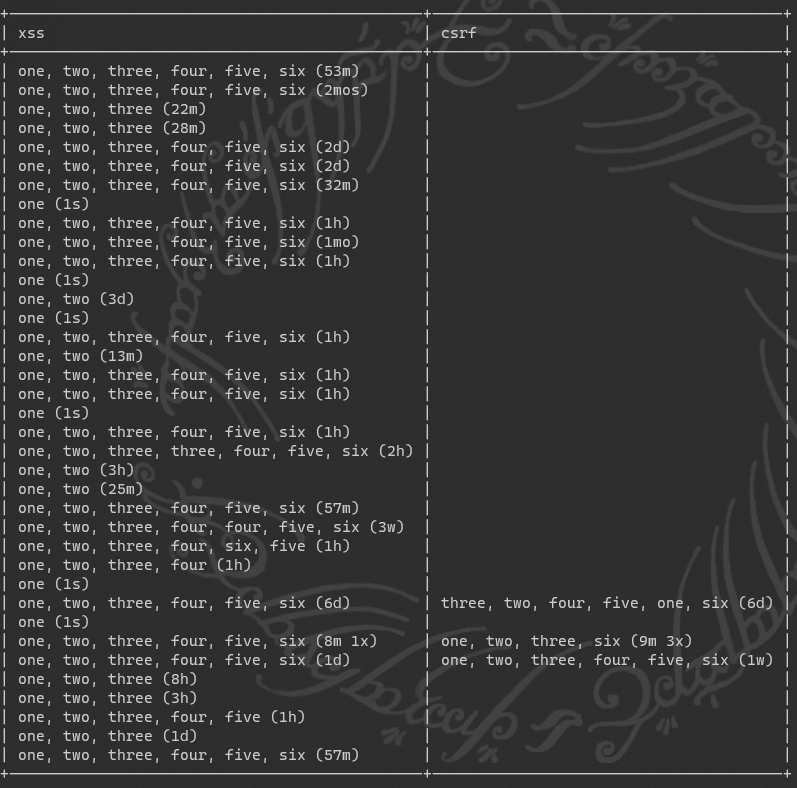
On the subject of challenges, here's how our leaderboard currently stands:
|
Lots of folks have completed the XSS challenges, but CSRF seems to have a lot of people stumped...
Can you solve the challenges?
Haven't Signed Up Yet?
If you haven't already purchased Practical Laravel Security, now is the perfect time to do so! With 7 modules released, and more coming very soon, you'll be able to dive right in and learn about all aspects of Laravel security!
The challenges are a big hit (especially the XSS ones!) - I've had a lot of great feedback about how they really aid in understanding each vulnerability. The upcoming SQLi challenges are going to be a lot of fun too, allowing you to really stretch your SQL skills!
The course also includes access to a private Discord server, where we've been having some awesome security discussion on a wide range of topics. There is a space to ask questions, if you need help with anything, and myself or one of the other course members can help you out. It's a really great group, and I'd love for you to join us! 🙂
Team licences are also available for teams of all sizes, reach out to me directly for the details! 😁
I also offer Student and PPP discounts - send me an email and I'll get you a discount code.
Until next time, I hope you have an awesome week! 😁
Thanks,
Stephen
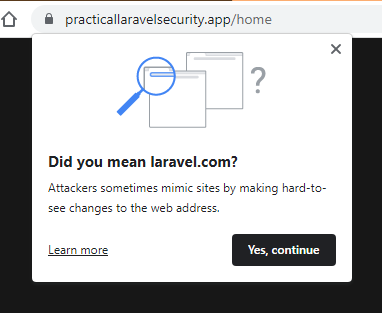
P.s. If you happen to see the "Did you mean laravel.com?" notice on one of the course domains, you can safely ignore it. It's an automated warning Google set up to find and alert on phishing or duplicated sites. I've submitted an appeal, so hopefully it'll disappear soon. 🤞
|
Even though it's showing up on my course domains, I find this type of warning super awesome. It's designed to help non-technical folks avoid being scammed online, and that's something I'm 100% for.