Do you know what Blind SQLi is?
Hey there!
Do you know what Blind SQLi is?
Blind SQLi is a method of SQL Injection attack where you cannot see any output form the query, and must instead rely on a different way to extract information through the vulnerable query. It's potentially tedious, but easily automatable. It's also the technique you'll need to use to conquer challenges #5 and #6 in the SQL Injection Attack module in my Practical Laravel Security course!
The best bit is, the SQL Injection (SQLi) Attack module is ready to go! I pushed it out early this evening, alongside the Parameterisation Defence module. If you've already signed up, you can check out the module here:
The SQLi module walks you through the different types of SQL Injection attacks and the primary defence of SQLi is covered in the Parameterisation module, plus there are 6 new challenges to teach you the different types of SQLi:
Challenge #1: Cliché Login SQLi (because I had to teach a chiché when dealing with SQLi...)
Challenge #2: Nested Login SQLi
Challenge #3: Union-Based SQLi
Challenge #4: Error-Based SQLi
Challenge #5: Blind Error-State SQLi 😈
Challenge #6: Blind Timing-Based SQLi 😈
They start out fairly easy, and get progressively harder. #5 and #6 are pretty involved, but you'll feel a huge sense of accomplishment when you get to the end. (I've also copied over the fireworks from XSS #6!)
If you'd like a bit of insight into the process behind building these challenges and some of the decisions I made, I wrote a Twitter (and Mastodon) thread covering the process. If you've any questions about the process, throw them onto the threads, or in our #challenges Discord channel.
What's Next?
The next modules I plan to tackle are encompassed under "Missing Authorisation", and will include things like Insecure Direct Object References (IDOR), and Laravel's Authorisation system. I'm still planning out how it'll be structured, but it's an important topic we need to dive into.
If there are any specific areas you'd like to especially focus on - or any attacks you'd like to see in a challenge - please let me know!
Haven't Signed Up Yet?
Practical Laravel Security is currently in Early-Access, which means you can sign up right now for a significant discount off the full price. You'll also get full access to the 9 released modules, and 18 challenges, plus access to our exclusive Discord server.
In the Early-Access right now you'll learn:
How to defend your apps from XSS attacks - including a few sneaky ways XSS finds its way into otherwise secure code.
How CSRF attacks occur due to misconfiguration and why subdomains cannot be trusted.
The various ways of abusing SQLi vulnerabilities, and why they are such a big deal.
So what are you waiting for?
There are Team Licences available for teams of all sizes, so please tell your team lead about Practical Laravel Security and encourage them to reach out to me directly for the details. 🙂
Until next time, I hope you have an awesome week!
Thanks,
Stephen
P.s. For those following the leaderboard updates, here is the latest:
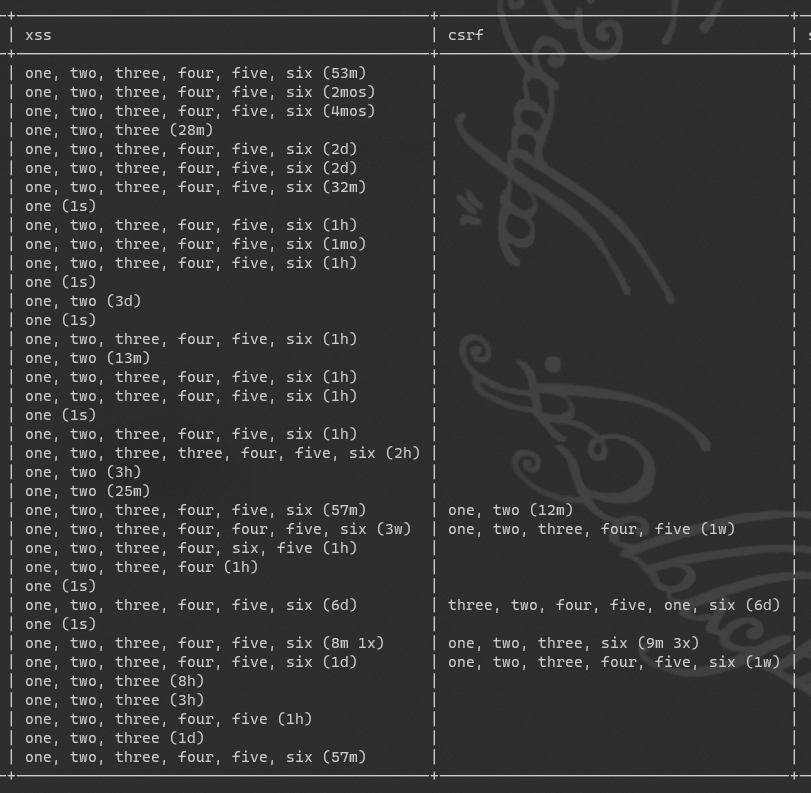
|
Looks like CSRF is contuining to stump folks, but there is a great showing for the XSS. I'll be keeping an eye on the SQLi logs!