Cross-Site Request Forgery... how big of a risk is it? (Plus, it's out!!)
Hey there,
I know I've been a bit quiet recently, but I'm very excited to let you all know that the new Practical Laravel Security Cross-Site Request Forgery (CSRF) module is now out! 🥳🎉
If you've already signed up, then you can head over right now to check it out!
If you haven't signed up yet, then what are you waiting for? 😉
Why Cross-Site Request Forgery?
Let's talk about CSRF, specifically, how big of a risk is it?
I ran a poll on Twitter and Mastodon, asking what folks think about CSRF. The results came back with 60-70% of devs leaving it up to the framework to deal with. And I can see why, especially in Laravel when the framework protects you by default!
Laravel gives us CSRF tokens out of the box, we've got SameSite=Lax cookies and the browser gives us Cross-Origin Resource Sharing (CORS). Combining these together than CSRF is not really a concern when you're building your app.
So why do we care?
As your app grows larger, you'll eventually need to support things like webhooks, API requests, cross-domain front-end requests, and more. There are a multitude of different reasons why you might need to disable CSRF tokens on a specific route, or open up CORS, or maybe even tweak the SameSite value.
This is where the risk is introduced, especially if you don't understand CSRF attacks. As you start disabling protections, weaknesses can be introduced if you open it up too wide, and this can lead to compromise.
CSRF Challenges
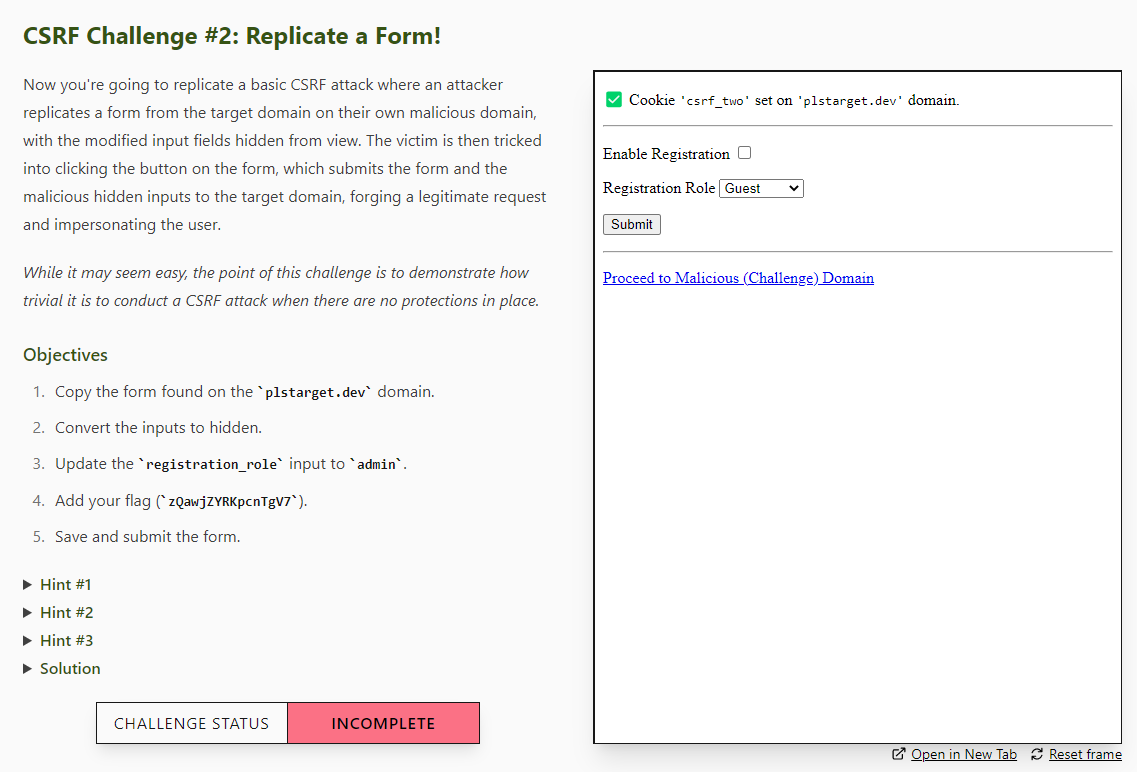
Just like the XSS module, the CSRF module comes with 6 challenges for you to work on. They follow the premise of: "what if some protections are disabled", and work you through escalating difficulty from a basic form right through to stealing and using a CSRF token in a single request!
When doing the challenges, I recommend you pop open the browser inspector and check out the network tab. By following the requests, headers, and cookies through the challenges, you'll gain a really good understanding of how CSRF attacks work and the mechanics of the different defences available.
As a sneak peak, challenge #2 requires you to replicate a provided form on the attack domain, modify the fields, and submit it. And if you think that sounds easy, just wait for #5 where you need to find a subdomain. 😉
|
What's Next?
Next up are the Defend modules that go alongside the CSRF Attack module:
CSRF Tokens
SameSite Cookies
Cross-Origin Resource Sharing (CORS)
These will fill in the pieces from CSRF, helping you keep your site secure.
After that, I plan to move onto the SQL Injection Attack module. 🤓
Ready to learn how CSRF and XSS attacks work?
Early-Access for Practical Laravel Security is open right now, at a heavily discounted price. With full access to released modules, you'll learn the essential security techniques you need to secure your Laravel apps.
Right now, Early Access includes modules on Cross-Site Scripting (XSS), Escaping Output, HTML and Markdown, and Cross-Site Request Forgery (CSRF) - with even more to come soon! Plus, you'll have access to challenging exercises to put your skills to the test.
Sign up now and start training your hacker skills through the XSS and CSRF challenges to keep your apps secure!
Please contact me directly forTeams pricing, as well as student and PPP discounts.
Good luck with the challenges! 😈
Thanks,
Stephen